What is LockBit 3.0, StealBit, BlackMatter, DarkSide ? Everything we should know!
LockBit ransomware, active since 2021, targets critical infrastructure supply chains using RaaS and StealBit for data theft and extortion. LockBit 5.0 evades detection across Win/Linux/ESXi. US offers $15M bounty. Mitigate with segmentation, MFA, and Dragos tools.

Disclaimer: The content of this article comprises information gathered from various publicly accessible sources. It is a condensed presentation, focusing on key points related to LockBit 3.0. The intention is to provide the dissemination of knowledge among security professionals to fortify their infrastructure against potential LockBit attacks. References to the original information security articles and blogs can be found at the bottom of this article.
LockBit ransomware attacks have been on the rise since 2021, especially targeting organizations linked to critical infrastructure or its supply chain. This trend continued into 2022, affecting various sectors like manufacturing, electric, transportation, and logistics.
The Department of State, United States is announced reward offers totaling up to $15 million for information leading to the arrest and/or conviction of any individual participating in a LockBit ransomware variant attack and for information leading to the identification and/or location of any key leaders of the LockBit ransomware group.
The folks behind LockBit use sneaky tactics to make victims more likely to pay up. One trick is stealing sensitive info from the victims using a tool called StealBit, made by the LockBit crew. They usually do this before encrypting the victim's systems with LockBit. If the victim doesn't cough up the ransom, the stolen data gets posted on the dark web, where other bad actors can use it for who-knows-what. If a capable attacker gets their hands on sensitive Operational Technology (OT) info from IT environment, it could lead to serious problems like direct attacks on OT systems, causing chaos, damage, or safety issues. There's even talk that LockBit might start using distributed denial of service (DDoS) attacks as another way to strong-arm victims.
Although there are no such record of attack seen that LockBit directly messing with Industrial Control Systems (ICS)/OT technology, the threat is still there. Many organizations with industrial setups could be in trouble if their business-critical systems, usually in the IT (Information Technology)/Enterprise environment, get compromised. LockBit has been hitting a lot of organizations relying heavily on ICS technology, suggesting they're picking victims based on who's more likely to pay. Since most industrial outfits depend on ICS tech and can't afford disruptions, they're prime targets.
Bottom Line:
- LockBit ransomware acts a lot like other ransomware that's messed with industrial setups.
- LockBit 3.0 can infect Windows systems, Linux systems, VMware vSphere, and ESXi virtual environments.
- Criminals have used LockBit 3.0 to hit manufacturing, electric, transportation, and logistics outfits.
- A ticked-off LockBit developer leaked the code for LockBit 3.0 in September 2022, helping researchers spot ways to defend against it.
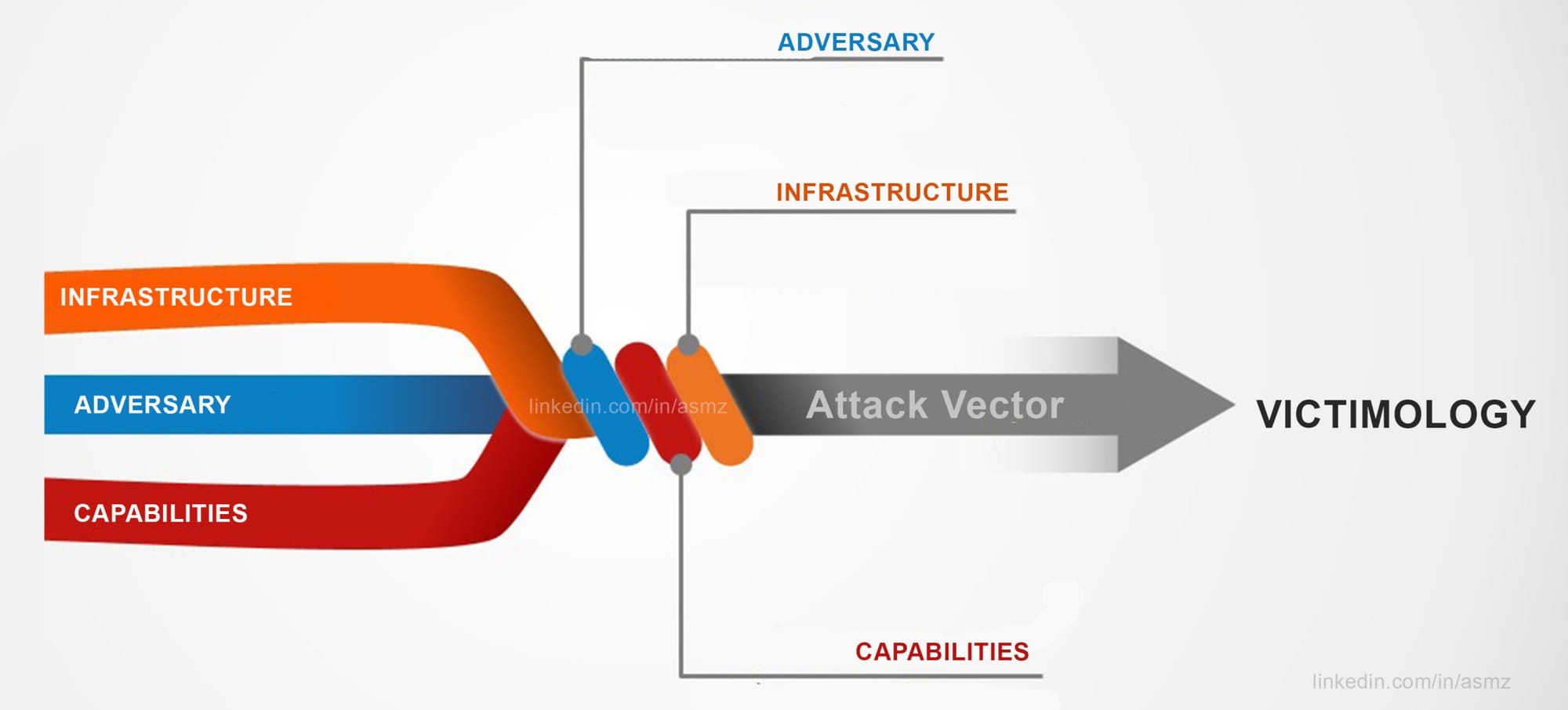
ADVERSARY
- Ransomware-as-a-Service with affiliate program
- Shares similarities with BlackMatter ransomware
INFRASTRUCTURE
- StealBit (information-stealing solution)
- Dark Web Resources
- Relies on penetration testing tools
CAPABILITIES
- Able to disable Windows Defenderand tamper with WindowsEvent Logs
- Bug bounty program
- Infects Windows systems, Linux systems, VMware vSphere, and ESXi virtual environments
- Double and Triple Extortion
VICTIMOLOGY
- Worldwide, concentrating on the U.S.
- Avoids post-Soviet countries
- Sectors include Retail, Electric, Manufacturing, Construction, Wholesale, Finance, Professional Services, Legal, Transportation, Technology, Consumer Services, Logistics
How it Operates ?
LockBit operates as a ransomware-as-a-service (RaaS) provider, emerging onto the scene in September 2019. Under this model, a central group designs the ransomware, which is then leased out to other criminal entities for their illicit activities. These entities, often termed affiliates, who obtain LockBit gain access not only to the ransomware itself but also to the necessary infrastructure for executing successful attacks. Profits stemming from LockBit activities are divided between these affiliates and the main orchestrators. Moreover, LockBit affiliates are incentivized to engage in a bug bounty initiative, rewarding individuals who identify flaws in the ransomware, vulnerabilities within the data leak platform, and those who successfully uncover the identity of the program's overseer. These supplementary benefits heighten the appeal of affiliating with LockBit while simultaneously bolstering the group's operational security. Initially recognized as the '.abcd virus' due to its characteristic file extensions upon encryption, LockBit evolved into LockBit 2.0 by June 2021. Subsequent updates introduced versions compatible with Linux systems and the VMware ESXi hypervisor, along with enhanced functionalities like self-propagation, log erasure, and the ability to print ransom notes on network printers until the paper supply depleted. [ Sources available at the bottom of this article]
LockBit 3.0 shares connections with other ransomware factions known for their impact on industrial systems, notably DarkSide and BlackMatter ransomware. The infamous Colonial Pipeline breach in May 2021 was attributed to these groups. Interestingly, LockBit 3.0 has earned the moniker "LockBit Black" in certain circles, a nod to its June 2022 iteration, which exhibited substantial code similarities with BlackMatter ransomware. Reports suggest a migration of talent within the cybercriminal community, with indications pointing towards a developer formerly affiliated with BlackMatter joining the LockBit team prior to the release of LockBit 3.0. Furthermore, beyond its roots in BlackMatter's codebase, LockBit 3.0 boasts additional functionalities and capabilities.
- Introduces a novel living-off-the-land (LOTL) tactic to bypass endpoint detection
- Capable of weaponizing legitimate security tools within compromised networks
- Implements a new anti-analysis method mandating unique passwords for each LockBit binary
- Increases encryption speed, allowing for more thorough host encryption before detection
- Incorporates distributed denial of service (DDoS) capability as an additional extortion tactic.
The BlackMatter ransomware exhibits similarities in features and configuration files with ALPHV, also known as Black Cat ransomware. In February 2022, members of the ALPHV ransomware group acknowledged their prior affiliation with the BlackMatter ransomware group. In July 2021, cybersecurity experts identified encryption algorithms in BlackMatter that linked it to the DarkSide ransomware family. Further investigation revealed that DarkSide developers rebranded their ransomware as BlackMatter following the Colonial Pipeline attack in May 2021. While the DarkSide operators did not penetrate Colonial Pipeline’s OT environment, the attack had significant repercussions, including disrupting critical business systems and hindering natural gas distribution pipeline maintenance. Shortly after this incident, DarkSide’s operators lost access to their infrastructure.
Victimology
LockBit saw a surge in activity throughout 2022, targeting various global organizations across sectors like manufacturing, transportation, and industry. Despite this, until December 2022, there hadn't been any confirmed instances of LockBit ransomware breaching OT (Operational Technology) systems. However, similar to other ransomware strains, LockBit operations pose a significant risk to critical business functions, often resulting in disruptions to services and supply chains. Notably, LockBit was particularly active in compromising industrial entities throughout 2021 and 2022, with Dragos' analysis indicating that LockBit 3.0 alone accounted for 21% of ransomware attacks, totaling 40 incidents in Q4 of 2022. Comparatively, other ransomware variants like Black Basta and Royal trailed behind, each comprising only 12% of the total incidents. Multiple cybersecurity experts have publicly stated their belief that LockBit will continue to pose a significant threat in the ransomware landscape.
In 2023, organizations heavily reliant on industrial infrastructure or providing critical services are more likely to succumb to ransom demands to prevent disruptions. For instance, many organizations lack visibility into crucial OT environments, making it challenging to detect ransomware attacks in this space. Insufficient segmentation could grant ransomware affiliates direct access to ICS devices for encryption. Additionally, the use of stolen credentials for initial access is prevalent, with a significant number of shared credentials between IT and OT systems observed in 2021. While enabling multi-factor authentication (MFA) is the most effective security measure, it may not always be feasible in industrial settings. Its also noted a notable rise in OT devices with external connections during engagements in 2021, which attackers exploit as convenient access points to networks.
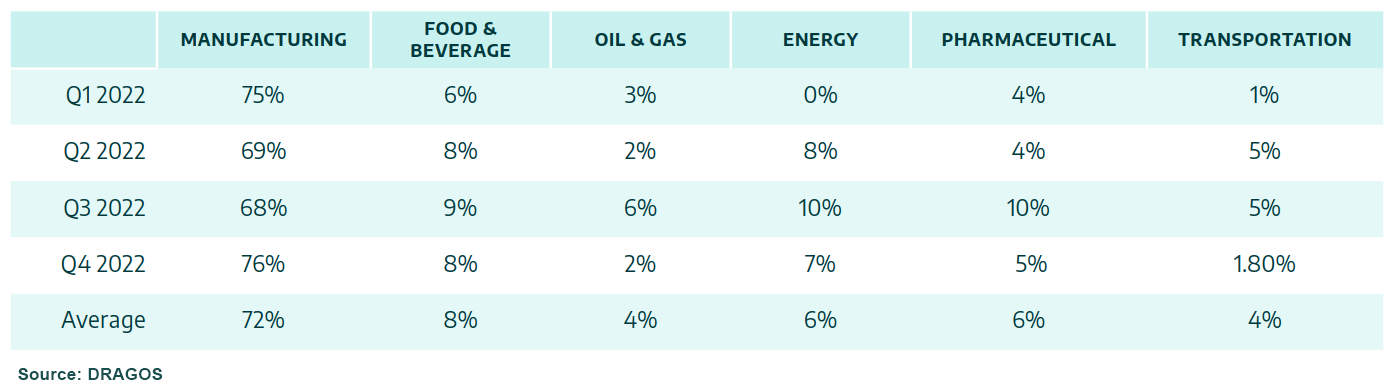
Ransomware attacks on the industrial sector have remained relatively constant over the past year. According to Dragos' analysis of ransomware attacks on ICS/OT systems, the manufacturing industry bore the brunt, accounting for 72% of total industrial ransomware attacks in 2022. Other sectors such as food and beverage, oil and gas, energy, pharmaceuticals, and transportation experienced varying percentages of ransomware attacks, ranging from 8% to 4% of the total attacks on industrial organizations. See Table 1 below for details.
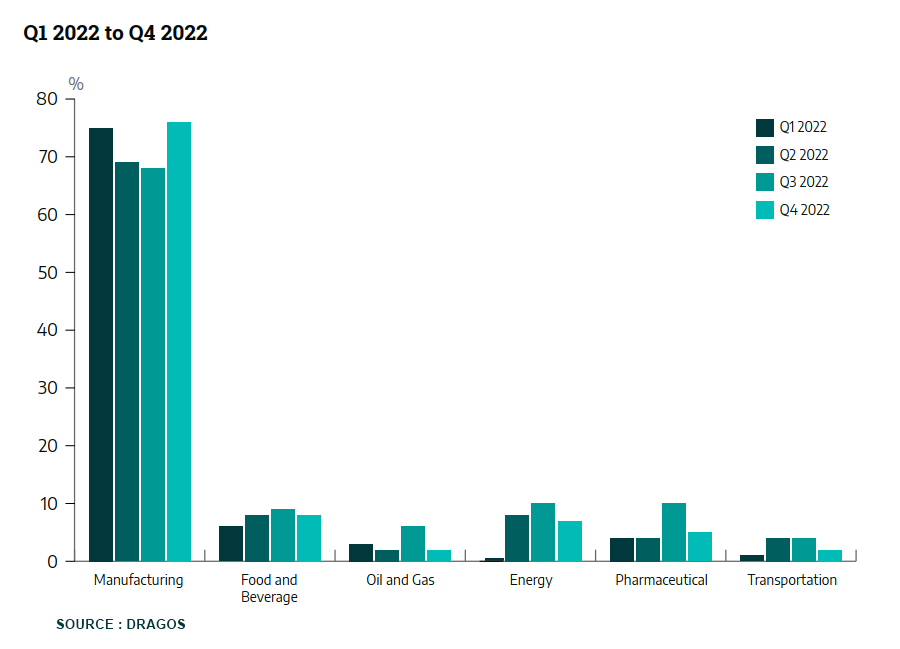
LockBit ransomware has emerged as the predominant threat to industrial targets since 2021, constituting an average of 31% of ransomware attacks directed at industrial sectors from the fourth quarter of 2021 onward. Following closely behind is Conti ransomware, which accounted for an average of 19% of such attacks. Notably, the data excludes the third quarter of 2022 due to Conti ransomware's cessation of operations and rebranding announced in May 2022.
From a geographical perspective, LockBit poses a global threat but has notably impacted a higher number of industrial organizations in the United States compared to other regions worldwide. It's worth mentioning that LockBit ransomware does not execute on operating systems set to Cyrillic as the default language and keyboard layout, a common configuration in the Commonwealth of Independent States (CIS) region. Despite this, there have been reports from Kaspersky Labs indicating that adversaries leveraged LockBit against Ukrainian organizations upon its introduction in 2019. The ransomware conducts a language check, terminating immediately if the user's language settings align with those internally listed within the malware.
Following are a timeline of LockBit operations against industrial companies between August 2021 and September 2022
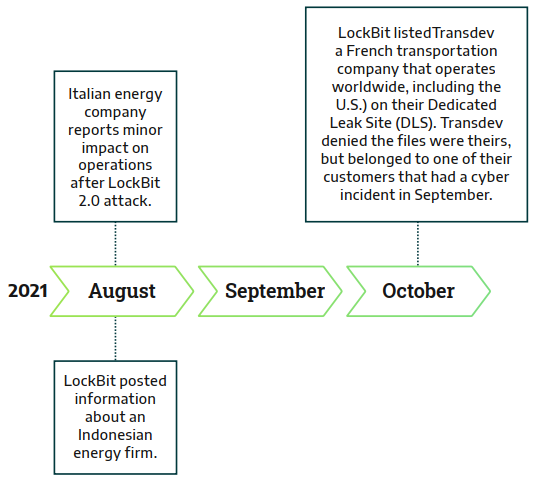
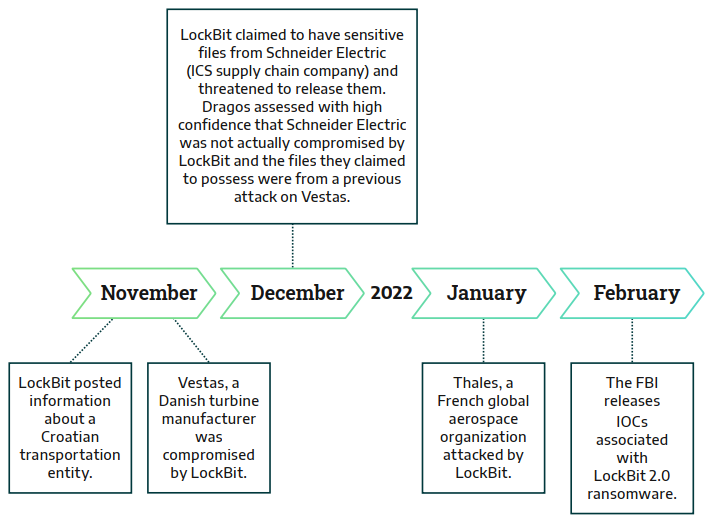
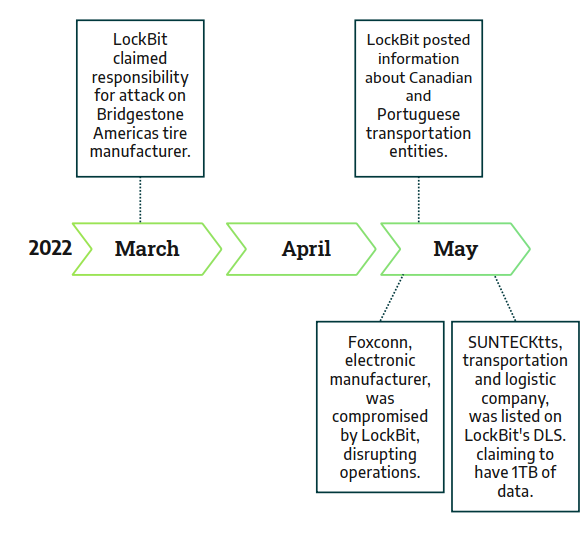
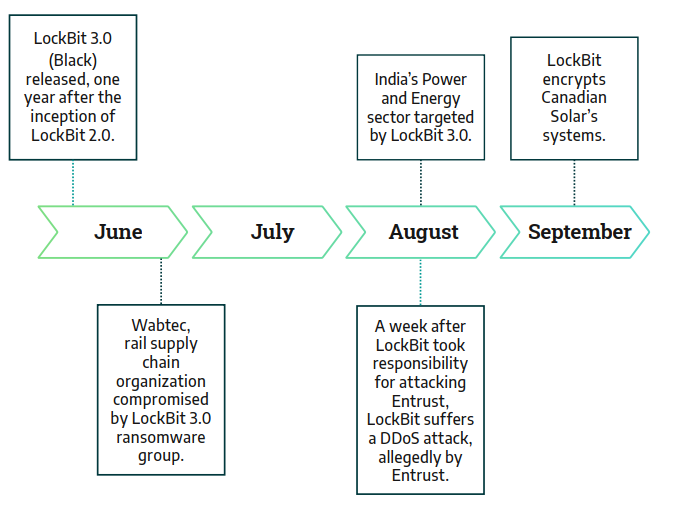
In its early days, LockBit primarily targeted healthcare organizations, causing significant impact. However, as LockBit gained traction, its operators diversified their targets, launching more attacks on manufacturing, transportation, aerospace, and food and beverage sectors in 2022. Despite LockBit developers implementing rules prohibiting the use of their ransomware against critical infrastructure, these rules are often ignored by affiliates. There seems to be little concern from LockBit developers about enforcing accountability among their affiliates. It's a common practice for ransomware developers to include ethical statements in their affiliate programs, aiming to distance themselves from unethical use of their products by operators, which unfortunately occurs frequently.
Capabilities
LockBit’s attack methodology is like other ransomware variants. Figure 4 summarizes the high-level stages of a LockBit attack collected from open-source research

The capabilities of LockBit ransomware are defined as the tools and techniques used throughout an attack. Each stage from Figure 4 is broken down into the tools, techniques, and associated MITRE tactics and techniques as documented from incident response and code analysis.
Initial Access
LockBit operators, akin to numerous ransomware factions, initially breach systems through familiar avenues such as phishing or spearphishing, exploiting vulnerabilities and zero-day weaknesses, leveraging compromised staff credentials, or procuring illicit entry via one of the numerous initial access brokers prevalent in the Darknet ecosystem. The subsequent diagram delineates LockBit's procedures for Initial Access and System Discovery.
System Discovery
After gaining initial access, LockBit ransomware employs various tools and methods to pinpoint weak spots within a network, facilitating its spread across a victim's system. Utilities like PC Hunter, Process Hacker, and GMER are utilized to shut down antimalware defenses. Additionally, the ransomware conducts system language assessments to verify that the victim's network doesn't belong to a CIS country, which LockBit affiliates refrain from targeting.
Persistence
Persistence is established by techniques to avoid detection, like anti-debugging and disabling services and tools that could identify and disable the ransomware. An adversary can use a Cobalt Strike beacon as a communication and remote execution tool.
Lateral Movement
LockBit gains access to a victim network by leveraging the connections and access points of the network's Domain Controllers and Active Directory. Utilizing acquired credentials obtained from the darknet or through penetration tools, the attacker establishes remote access and subsequently infiltrates the network.
Exfiltration and Encryption
The developers behind LockBit have showcased their adeptness and readiness to craft bespoke tools, as evidenced by the creation of StealBit. This information-stealing tool supplements LockBit 2.0's service offerings, serving as a data exfiltration tool and the primary conduit for their double-extortion capability. StealBit boasts impressive data exfiltration rates by enabling simultaneous theft of multiple files and employing interprocess communication (ICP) among its processes running on compromised systems.
A notable feature of LockBit 3.0 is its encryption efficiency. Regarding ransomware encryption speeds, there are two prevailing perspectives:
- Slow Encryption: Deliberately designed to operate discreetly within the victim's network to avoid detection.
- Fast Encryption: Although more conspicuous to network defenders due to its speed, it may go unnoticed until it's too late, owing to the rapid encryption pace.
LockBit maintains swift encryption rates by encrypting only the initial 4KB of a file and appending an extension "HLJkNskOq." Upon execution, LockBit encrypts victims' files using the Advanced Encryption Standard (AES), and subsequently encrypts the AES key further using the RSA algorithm. Following the encryption process, the victim's background is altered, and the ransom note starts printing on locally networked printers.
Infrastructure
LockBit maintains DWRs on TOR where stolen documents and information are published from victims that refused to pay the ransom. They accept multiple forms of payment on their DWRs, such as Monero, bitcoin, and Zcash. Other third-party criminals can purchase the stolen data from their DWRs, as well, however, this feature does not appearto be fully operational at the time of this report. Third-party criminals interested in buying stolen information advertised on their DWRs could just as easily connect with the LockBit purveyors directly through peer-2-peer channels.
Detection and Mitigations
In late September 2022, LockBit’s builder was released, supposedly by one of their own disgruntled developers. Security vendor's Detection and Vulnerability teams, continue to analyze the code to provide detections to network defenders.
The following signatures from open source research are still under development, and they has not evaluated them for accuracy.
- Florian Roth is actively developing working Yara signatures:
- MAL_RANSOM_Lockbit_3_Jul22_127
- MAL_RANSOM_Lockbit_Embedded_Jul22_228
- Malpedia Yara rule detects win.lockbit29
Conclusion
LockBit Ransomware-as-a-Service (RaaS) continues to pose a significant threat to critical infrastructure, both directly and indirectly. When supply chain manufacturing companies are targeted, it can easily lead to service or product disruptions that critical infrastructure heavily relies on. Moreover, the fact that LockBit shares code with BlackMatter and, consequently, DarkSide represents a pivotal moment in showcasing how genuine ransomware attacks can severely affect the operational processes and systems of critical infrastructure organizations, leading to substantial financial and reputational losses.
Furthermore, an important observation about LockBit's operations is its more strategic approach to victim selection. It's not merely about attacking as many organizations as possible; there's a discernible method behind it. The Colonial Pipeline incident underscored to ransomware operators that critical infrastructure organizations may be more inclined to pay the ransom if their operations are directly impacted.
SOURCES & CREDITS :
- PALO ALTO - LockBit 2.0: How This RaaS Operates and How to Protect Against It - https://unit42.paloaltonetworks.com/lockbit-2-ransomware/#tactics-techniques-procedures
- Ransomware review: September 2022 - https://www.malwarebytes.com/blog/threat-intelligence/2022/10/ransomware-review-september-2022
- LockBit Ransomware Group Augments Its Latest Variant, LockBit 3.0, With BlackMatter Capabilities - https://www.trendmicro.com/en_us/research/22/g/lockbit-ransomware-group-augments-its-latest-variant--lockbit-3-.html
- LockBit ransomware mulls triple extortion following DDoS attack - https://www.scmagazine.com/brief/lockbit-ransomware-mulls-triple-extortion-following-ddos-attack
- BlackCat (ALPHV) ransomware linked to BlackMatter, DarkSide gangs – BleepingComputer- https://www.bleepingcomputer.com/news/security/blackcat-alphv-ransomware-linked-to-blackmatter-darkside-gangs/
- DarkSide ransomware gang returns as new BlackMatter operation – BleepingComputer - https://www.bleepingcomputer.com/news/security/darkside-ransomware-gang-returns-as-new-blackmatter-operation/
- LockBit, Conti most active ransomware targeting industrial sector - https://www.bleepingcomputer.com/news/security/lockbit-conti-most-active-ransomware-targeting-industrial-sector/
- DarkSide ransomware gang returns as new BlackMatter operation - https://www.bleepingcomputer.com/news/security/darkside-ransomware-gang-returns-as-new-blackmatter-operation/
- Dragos Industrial Ransomware Analysis: Q4 2022 - https://www.dragos.com/blog/industry-news/dragos-industrial-ransomware-analysis-q4-2022/
- Conti ransomware shuts down operation, rebrands into smaller units - https://www.bleepingcomputer.com/news/security/conti-ransomware-shuts-down-operation-rebrands-into-smaller-units/
- LockBit ransomware — What You Need to Know - https://www.kaspersky.com/resource-center/threats/lockbit-ransomware
- LockBit Ransomware -https://www.blackberry.com/us/en/solutions/endpoint-security/ransomware-protection/lockbit
- LockBit: Ransomware Puts Servers in the Crosshairshttps://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/lockbit-targets-servers
- LockBit, Conti most active ransomware targeting industrial sector – BleepingComputerhttps://www.bleepingcomputer.com/news/security/lockbit-conti-most-active-ransomware-targeting-industrial-sector/
- Dragos Industrial Ransomware Analysis: Q3 2022 – Dragoshttps://www.dragos.com/blog/industry-news/dragos-industrial-ransomware-analysis-q3-2022/
- Dragos Industrial Ransomware Analysis: Q2 2022 – Dragoshttps://www.dragos.com/blog/dragos-industrial-ransomware-analysis-q2-2022/Dragos
- ICS/OT Ransomware Analysis: Q1 2022 – Dragoshttps://www.dragos.com/blog/industry-news/dragos-industrial-ransomware-analysis-q1-2022/
- Dragos ICS/OT Ransomware Analysis: Q4 2022 – Dragoshttps://www.dragos.com/blog/industry-news/dragos-ics-ot-ransomware-analysis-q4-2021/
- Dragos Industrial Ransomware Analysis: Q4 2022 – Dragoshttps://www.dragos.com/blog/industry-news/dragos-industrial-ransomware-analysis-q4-2022/
- Conti ransomware shuts down operation, rebrands into smaller units - BleepingComputerhttps://www.bleepingcomputer.com/news/security/conti-ransomware-shuts-down-operation-rebrands-into-smaller-units/
- LockBit ransomware — What You Need to Know – Kasperskyhttps://www.kaspersky.com/resource-center/threats/lockbit-ransomware
- LockBit Ransomware: A Guide – BlackBerryhttps://www.blackberry.com/us/en/solutions/endpoint-security/ransomware-protection/lockbit.
- LockBit: Ransomware Puts Servers in the Crosshairs – Symantechttps://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/lockbit-targets-serversAn interview with LockBit: The risk of being hacked ourselves is always present – The Recordhttps://therecord.media/an-interview-with-lockbit-the-risk-of-being-hacked-ourselves-is-always-present/
- Ransomware Spotlight LockBit – Trend Microhttps://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-lockbit
- The State of Ransomware in Healthcare 2022 – Sophoshttps://assets.sophos.com/X24WTUEQ/at/4wxp262kpf84t3bxf32wrctm/sophos-state-of-ransomware-healthcare-2022-wp.pdf
- LockBit ransomware builder leaked online by “angry developer”– BleepingComputer https://www.bleepingcomputer.com/news/security/lockbit-ransomware-builder-leaked-online-by-angry-developer/
- MAL_RANSOM_Lockbit_3_Jul22_1– Valhallahttps://valhalla.nextron-systems.com/info/rule/MAL_RANSOM_Lockbit_3_Jul22_1
- MAL_RANSOM_Lockbit_Embedded_Jul22_2– Valhallahttps://valhalla.nextron-systems.com/info/rule/MAL_RANSOM_Lockbit_Embedded_Jul22_2
- Win.lockbit– Malpediahttps://malpedia.caad.fkie.fraunhofer.de/details/win.lockbit
